Getting Windows Server L2TP VPN, with IPSEC behind NAT, working in Gnome Network Manager
Published by John on August 27, 2020 Under SysadminRecently, I ran into a few issues using the StrongSwan L2TP Gnome NetworkManager VPN connection working, specifically while the Server and Remote Client are behind a NAT firewall.
There were two main issues, the first was the wrong remote ID, as by default this type of VPN is not expecting to be behind a NAT device.
This results in an error like this:
#1: we require IKEv1 peer to have ID 'XXX.XXX.XXX.XXX', but peer declares 'YYY.YYY.YYY.YYY' #1: sending encrypted notification INVALID_ID_INFORMATION to XXX.XXX.XXX.XXX:4500
In this example, ‘XXX.XXX.XXX.XXX’ is the public IP address of the VPN server and ‘YYY.YYY.YYY.YYY’ is the private IP address of the VPN server. To fix, set the ‘Remote ID’ on the VPN client to the private IP address of the server(YYY.YYY.YYY.YYY).
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\PolicyAgent] "AssumeUDPEncapsulationContextOnSendRule"=dword:00000002
After that, the two NAT devices would talk, but I still had to disable Perfect Forward Security, PFS, as well as change a couple authentication settings to get it to work.
Below are the settings I used to make the connection:
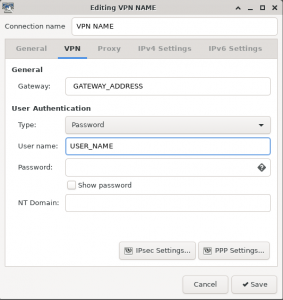
General Settings:
Gateway: The IP/Domain of Windows VPN Server
Username: VPN Client User
Password: Ask For this Password Each Time
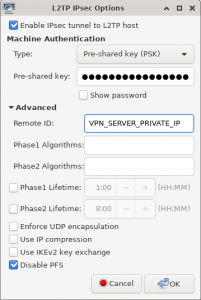
IPsec Settings:
Enable IPsec tunnel to L2TP host: Checked
Type: Pre-Shared Key (PSK)
Advanced -> Remote ID: The Private IP of the VPN Server
Advanced -> Disable PFS: Checked
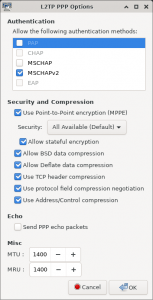
PPP Settings:
Allow the following authentication methods: MSCHAPv2
Use Point-to-Point encryption (MPPE): All Available
Allow stateful encryption: Checked
All other boxes checked, except ‘Send PPP echo packets’, which was the default when setting this up.
After this, I was able to connect without issue to the Windows Server VPN, using the Gnome Network Manager plugin in Linux.
No Comments |

Add a Comment